POODLE Attack Capable of Bypassing Some TLS Installations
SSLv3 is dead and POODLE killed it. After news of the attack was made public web administrators were urged to finally disable SSLv3 and only use TLS for secure communications. But the security gods are cruel. It turns out that some installations of TLS are vulnerable to the POODLE attack as well:
On Monday, word emerged that there's a variation on the POODLE attack that works against widely used implementations of TLS. At the time this post was being prepared, SSL Server Test, a free service provided by security firm Qualys, showed that some of the Internet's top websites—again, a list including Bank of America, VMware, the US Department of Veteran's Affairs, and Accenture—are susceptible. The vulnerability was serious enough to earn all sites found to be affected a failing grade by the Qualys service.
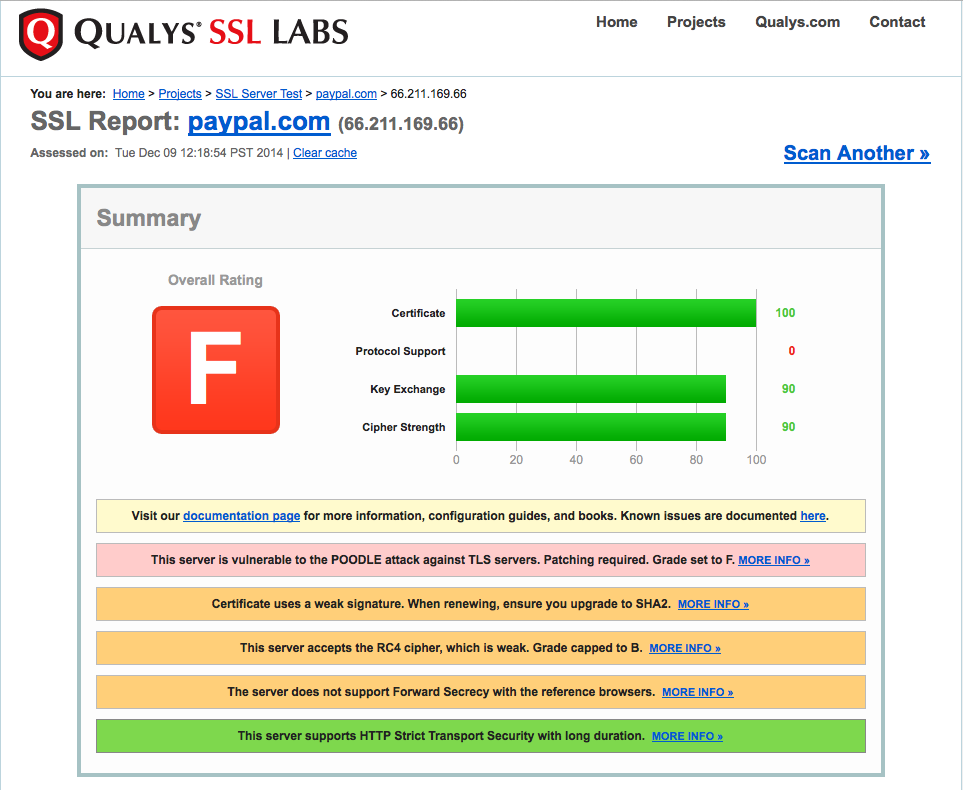
Qualys's SSL Labs testing tool is a wonderful piece of software. It tests for various SSL vulnerabilities including this new POODLE exploit. Using it I was able to confirm, quite happily, that this site is not vulnerable (check out that sexy A rating). But I'm a dick so I also checked a few other sites to see what everybody else was doing. My favorite result was Paypal's gigantic F rating:
Paypal is a major online transaction provider. You would think that their server administrators would be keeping everything as locked down as possible. But they're apparently sleeping on the job. It should be embarrassing to a company like Paypal that a single individual running a few hobby sites has tighter security.
But if you administer any websites you should check your setup to make sure your security connections are up to snuff (and unsecured connections are disabled entirely because it's 2014 and nobody should be communicating across the Internet in the clear).